How to protect PHP, JS, HTML, CSS source code - obfuscation, minification, compression and encryption
Sometimes it is necessary to hide the source code from view and easy analysis by outsiders. Most often, this applies to non-compiled programming languages and open source document markup tools. Since in the case of compiled means, the output is binary code, which is difficult to return to a human-readable code. project protection in PHP, JS, HTML, CSS may be especially relevant.
It is generally believed that what comes to the user is impossible to protect. It is argued that this is in vain and it is proposed to leave everything in the open. But this is usually misleading. There is a pattern - any action gives rise to a reaction, and everything was once impossible, so you should not pay much attention to such statements. If someone has not achieved, it does not mean that you cannot - such is the nature of inventions.
With a proper approach to protecting your code, you can get a certain minimum of protection, which may be sufficient - since not everyone has great knowledge and experience in development, which means that deobfuscation and understanding deobfuscated code will become a difficult task for them. Even if the product gets to a professional, he will not open it if he is conscientious. The rest, although they can hack the product and get an approximate source code, but their number may not be so large and this is still a violation and can be prosecuted by law if certain conditions for using the software product are established.
In other words, even if you use open development tools, the source code does not have to be as open and understandable to others, with comments and explanations - perhaps your task was just to write obfuscated code and criticizing that you wrote bad code ("shit code", dirty code, etc.) would be inappropriate.
Several operations can be applied for protection - obfuscation, minimization, compression, encryption, etc. It is important to separate these concepts, since it is often the division of a task into subtasks that is the success in achieving the goal.
You can start with obfuscation - make the code look incomprehensible. To do this, you can use the lexical analysis of the programming language and its representation in tokens - this is applicable just for the PHP language (there is a special function token_get_all). Then these lexemes are analyzed and, depending on the value, their names are substituted. As the code is processed, a special array of exceptions can be formed - which functions, variables and constants do not need to be renamed for any reason. Also, arrays with exclusion rules can be added manually in the obfuscator settings. As a result, when replacing names, all exceptions should be taken into account and the required level of obfuscation will be obtained. Obfuscation in JS is similar, but you need to develop and use your own language lexer to select specific types of language constructs. For HTML, CSS obfuscation, it will usually involve renaming the class names in an obscure way.
Missing pieces of junk code can be inserted into the code to obfuscate. In general, this topic is extensive and, with the proper approach, a high-quality obfuscator can be implemented, after which deobfuscation will be almost impossible. To do this, you can resort to various sophistications. But for most projects, a basic obfuscation will probably be enough - which will serve as a signal to conscientious users that it is not allowed to open your code.
Code minification can be applied as the next step in code protection. It means removing all spaces and line breaks where it is appropriate and will not harm the code. The output will be compact code, which is already difficult to understand when simply opened in the editor. In addition, minimization (or minification) reduces the size of the code file, which has a positive effect on the download and processing speed of such files. This step is applicable to various development tools: PHP, JS, HTML, CSS, etc.
Compress or encrypt the code - can be applied as the last step of protection. Compression can be done natively in the programming language, for example PHP has the function base64_encode and the reverse base64_decode. But because of this, antiviruses may mistake your code for infected and will receive notifications from the hoster (seen on some hosting sites, for example, with Virusdie antivirus on reg.ru). Agree, such a project is harder to distribute if the user sees warnings about viruses, even if they are false. Therefore, you can implement your own means of compression or encryption. This stage is also relevant for all development tools.
Off-the-shelf tools can often be used to obfuscate and protect code, but their prevalence is a vulnerability, since there are similar deobfuscators for popular obfuscators. Therefore, you should use your own designs for greater protection.
Reverse actions - deobfuscation, deminimization, decompression and decryption. Although deobfuscation will allow you to get the source code, it will not be restored to its original form - with all the spaces and hyphens as in the original, as well as with the original names of variables and functions. This means that it will be a different code, it will not be a copy of the original.
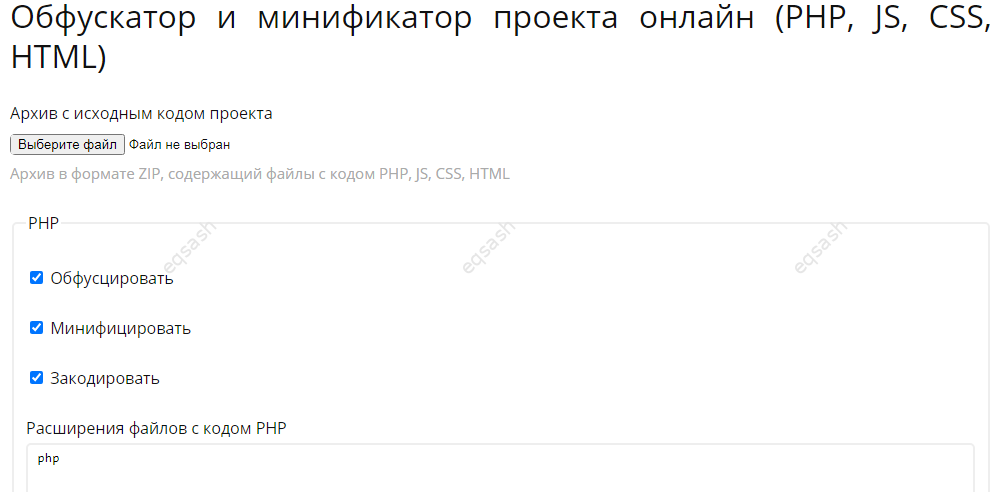
Should obfuscation - yes, if you need to hide the source code. But the final level of security will depend on how obfuscation is implemented. This resource has an obfuscation service - you can use it for free online at the link " Online project obfuscator and minifier (PHP, JS, CSS, HTML)". Its peculiarity is that you can download and obfuscate the entire project, select the desired settings, set exceptions, etc.
Latest articles
- 03.04.24IT / Уроки PHP Уроки простыми словами. Урок 3. Все операторы PHP с примерами, с выводом работы кода на экран.
- 02.04.24IT / Уроки PHP Уроки простыми словами. Урок 2. Типы данных в PHP с примерами.
- 02.04.24IT / Уроки PHP Уроки простыми словами. Урок 1. Коротко о языке веб-программирования PHP. Основы синтаксиса.
- 09.11.23IT / Database Errors when migrating from MySQL 5.6 to 5.7 and how to fix them - database dump import failed with an error or INSERT does not work. Disabling STRICT_TRANS_TABLES strict mode or using IGNORE
- 08.07.22IT / Misc Convert office files DOC, DOCX, DOCM, RTF to DOCX, DOCM, DOC, RTF, PDF, HTML, XML, TXT formats without loss and markup changes
 10101
10101