List content in category "IT / Safety"
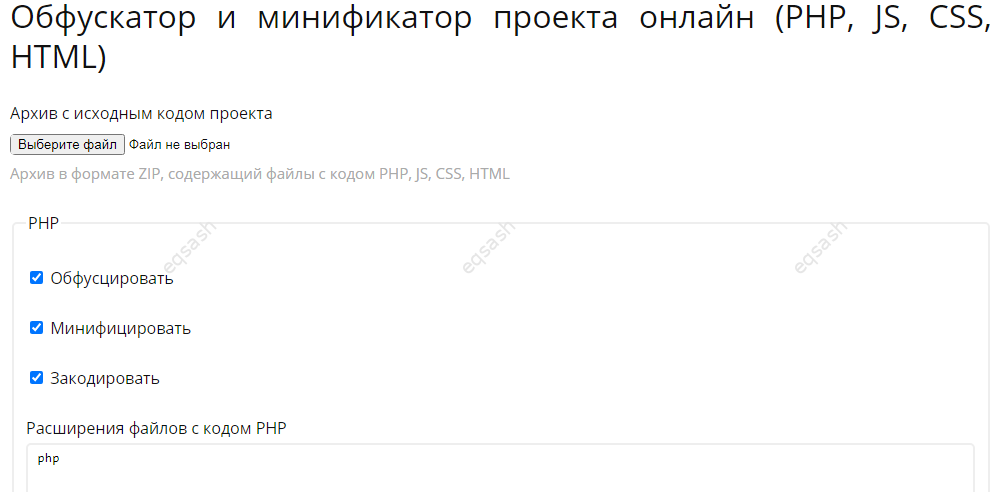
How to protect PHP, JS, HTML, CSS source code - obfuscation, minification, compression and encryp...
Sometimes it is necessary to hide the source code from view and easy analysis by outsiders. Most often, this applies to non-compiled programming la...
05.03.24
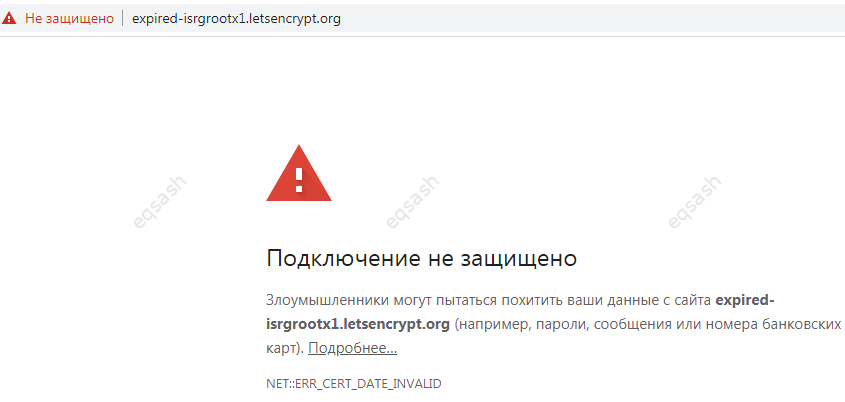
Connection not secure, problem with Lets Encrypt - how to fix expired 09/30/2021 DST Root CA X3, ...
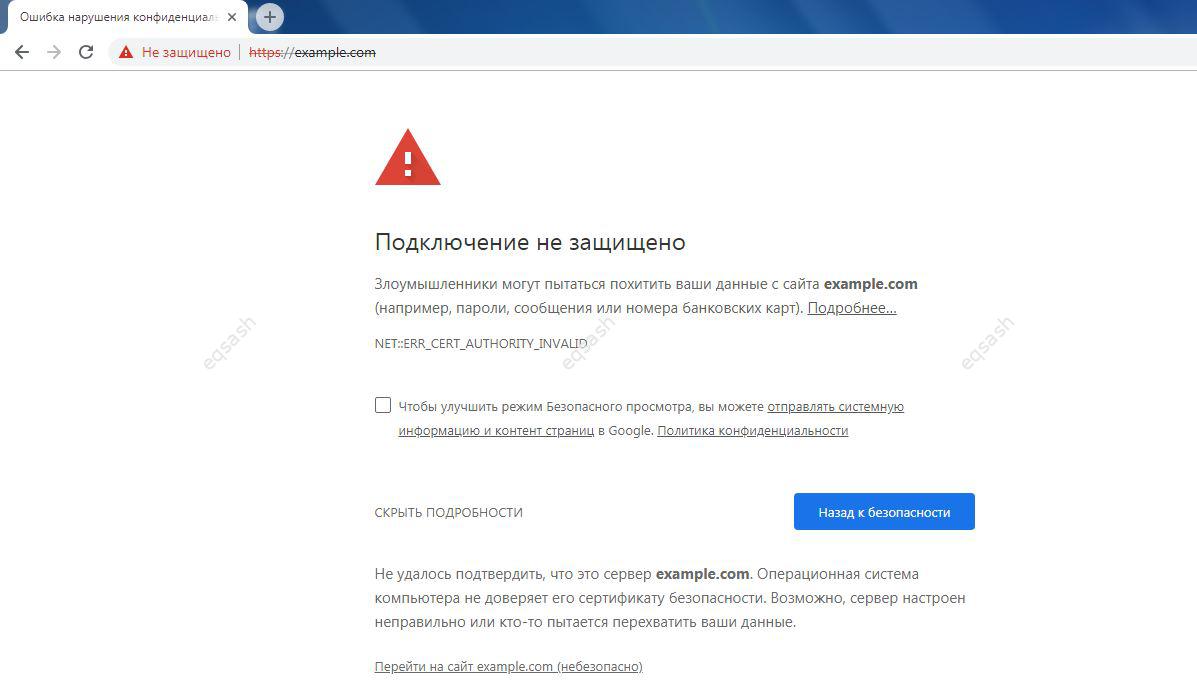
If a warning appears with a red icon when entering the site "The connection is not secure, the certificate has expired" - then the reason may be th...
16.07.22
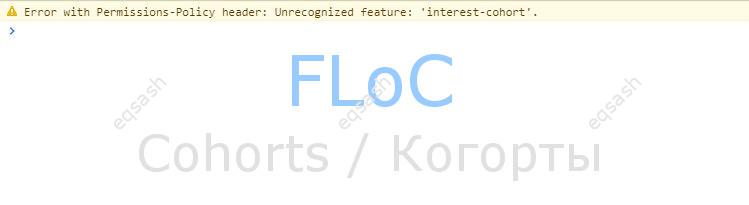
Google Cohorts are just groups that are formed according to certain preferences. In contrast to the orientation for one user, it is much easier ...
16.07.22
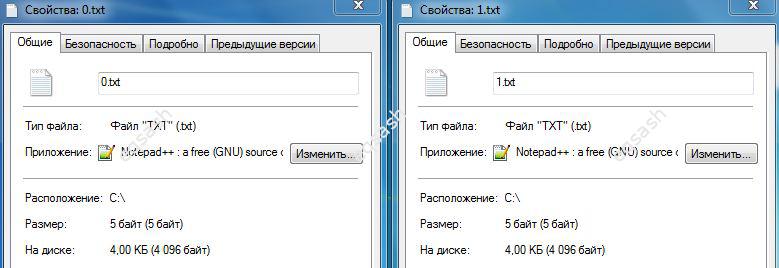
Information is distributed by copying, downloading a file is also copying. Sometimes errors can occur during the copy process, due to which the co...
17.07.22
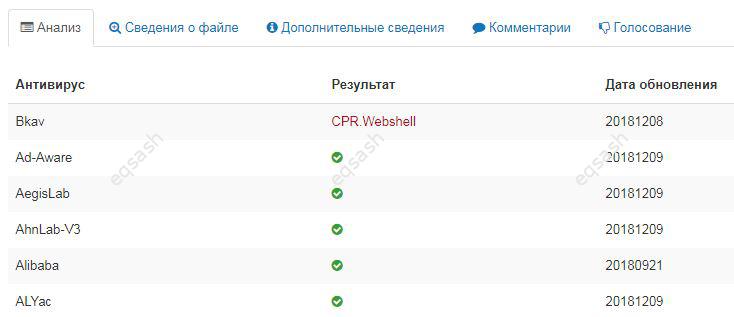
If there are doubts about the safety of the visited resource on the network, you can always use online virus scanners. The advantage of such servi...
17.07.22
Sometimes it is required to check the site for viruses, for this many use various means in this area. But they are often ineffective, and can even...
17.07.22
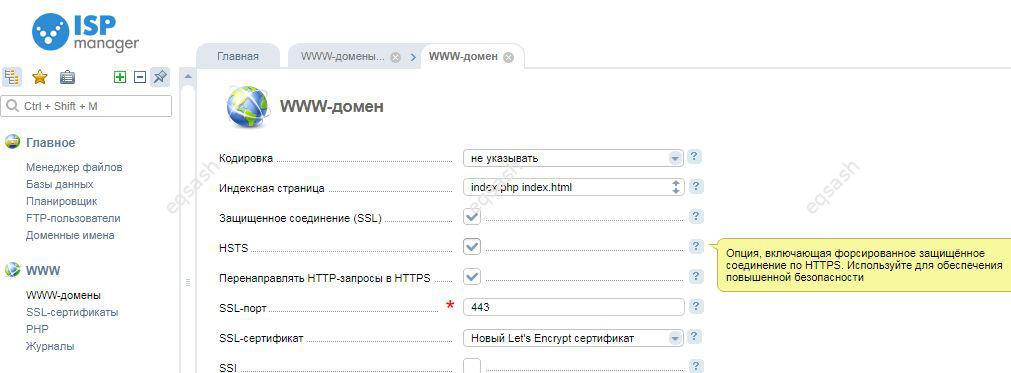
It may be necessary to test the operation of a web application or site via HTTPS, especially for developing sites on a local PC. Moreover, at pres...
05.03.24
After the general introduction of the HTTPS protocol, it became necessary in some way to redirect site visitors to open pages through this protoco...
17.07.22
Currently, any tool can be used not only by a living person, but also by robots created by him. Robots are being introduced everywhere, they are d...
18.07.22
Today, sites without encryption of the connection are generally recognized as insecure, so there is a need to transfer them to a secure connection...
18.07.22
The modern realities of the development of information technologies and laws in the country require the use of special tools for effective work wi...
18.07.22
With the development of technology, the methods of interception of information by intruders are also developing. Not so long ago, the problem of r...
19.07.22
Hackers use all sorts of techniques and methods to gain access to user data. One such technique is phishing. The word phishing comes from the Engl...
19.07.22
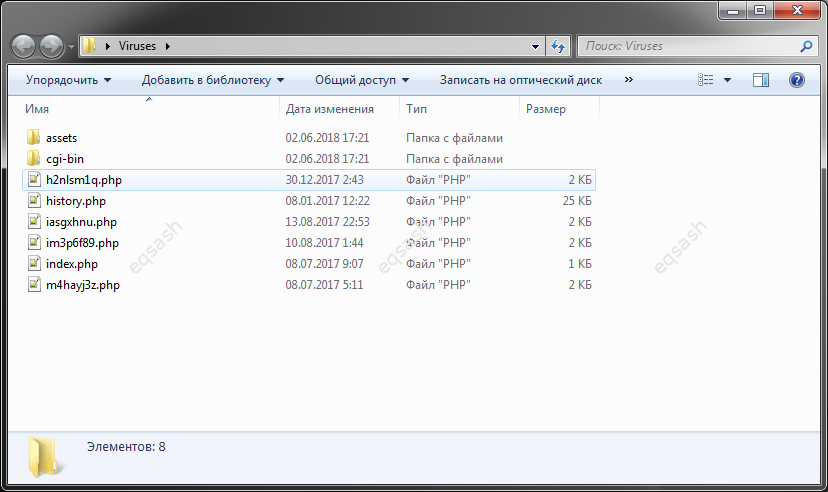
Currently, site hacking is quite common. This can happen at any time and no one is immune from this. A hack may not be detected immediately, and t...
19.07.22
Do I need to update the site - why is it so important. How to update the site, its modules and th...
Site security depends on many criteria, one of which is timely software updates. This includes updating the CMS, its modules, themes and other sof...
19.07.22
Site security is currently one of the most important areas that requires serious attention. According to the data, hacking sites by various pers...
19.07.22
Now basically all sites have the htpps protocol , which replaced the http . What caused this? The https protocol is the same http, only th...
21.07.22
Sometimes a situation may arise when the site starts to work differently than before, some oddities in its work become noticeable. This could be a...
21.07.22
Оставить заявку
Latest articles
- 03.04.24IT / Уроки PHP Уроки простыми словами. Урок 3. Все операторы PHP с примерами, с выводом работы кода на экран.
- 02.04.24IT / Уроки PHP Уроки простыми словами. Урок 2. Типы данных в PHP с примерами.
- 02.04.24IT / Уроки PHP Уроки простыми словами. Урок 1. Коротко о языке веб-программирования PHP. Основы синтаксиса.
- 09.11.23IT / Database Errors when migrating from MySQL 5.6 to 5.7 and how to fix them - database dump import failed with an error or INSERT does not work. Disabling STRICT_TRANS_TABLES strict mode or using IGNORE
- 08.07.22IT / Misc Convert office files DOC, DOCX, DOCM, RTF to DOCX, DOCM, DOC, RTF, PDF, HTML, XML, TXT formats without loss and markup changes