Checking and treating the site from viruses
Sometimes a situation may arise when the site starts to work differently than before, some oddities in its work become noticeable. This could be a sign of a virus infection of the site. In this case, you must immediately check the site for viruses and start curing in case of infection.
What are the consequences of hacking? Variety. For example, the site will be closed and malicious code will be placed, which will already infect the computers of visitors and extort money. Or all data will be stolen and transferred to your competitors. There are many options for the development of events, so it is necessary to quickly stop hacking.
It is important to understand that if other sites are located near the site, hacking could be done through them, or vice versa, they can also be hacked through the current site. Therefore, all verification and treatment steps must be performed for all sites on the same hosting account.
How to scan a site for viruses ? There are many verification services on the Internet, and hosting services offer special services. But as a recent case has shown, they may not always detect an infection. In this case, you should contact a specialist. A qualified specialist will be able to quickly check the site and cure it.
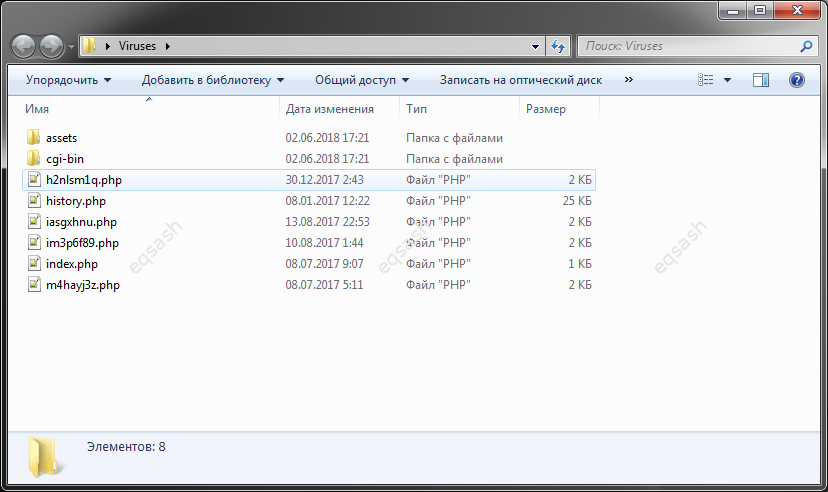
What should you pay attention to? First of all, you need to browse the main directories of the site through ftp . If unfamiliar extraneous files and folders appear, this is a sign of infection . In the administrative part of the site, you need to check the basic settings to see if something superfluous has appeared there, for example, new roles and users. It is important to look at the contents, their modified dates. If unauthorized access to the site is detected, it is necessary to immediately start repelling attacks in real time.
Perhaps, at the moment of detection of outside interference, the attacker performs the initial stage of hacking, after which the site will be completely taken out of work. Therefore, it is imperative to start monitoring and mitigating attacks immediately.
You can put the site into maintenance mode and start online recovery of the site from a backup copy, having previously made a backup of the current state so that you can further study the site's vulnerabilities and the hacking techniques used. You also need to start adding ip-addresses from which the hacking takes place in the blacklist, or rather address ranges, since often the addresses change dynamically.There is such a problem when even the restored site is still infected, since the infection occurred a long time ago. This can happen if you do not make backups yourself, and the hosting may have a short storage period for backups. In this case, you will have to manually delete malicious folders and files, as well as check all system files for intrusion of foreign code. You will also have to analyze the database and the administrative part of the site for malicious code.
But even if everything is successfully repaired, if the vulnerability was not found and fixed, hacking will be repeated . Therefore, it is important to restore all these sites and immediately eliminate the vulnerability, it is better to do it all on a local PC, and then transfer it to hosting. This will protect against new hacks while the vulnerability is fixed. For example, you may need to update the system (CMS) on which the site or its modules and themes are running.
After completing the above steps, you can restore the site to work. If you are unable to get rid of viruses on the site, you can ask for help through the feedback on this site.
Latest articles
- 03.04.24IT / Уроки PHP Уроки простыми словами. Урок 3. Все операторы PHP с примерами, с выводом работы кода на экран.
- 02.04.24IT / Уроки PHP Уроки простыми словами. Урок 2. Типы данных в PHP с примерами.
- 02.04.24IT / Уроки PHP Уроки простыми словами. Урок 1. Коротко о языке веб-программирования PHP. Основы синтаксиса.
- 09.11.23IT / Database Errors when migrating from MySQL 5.6 to 5.7 and how to fix them - database dump import failed with an error or INSERT does not work. Disabling STRICT_TRANS_TABLES strict mode or using IGNORE
- 08.07.22IT / Misc Convert office files DOC, DOCX, DOCM, RTF to DOCX, DOCM, DOC, RTF, PDF, HTML, XML, TXT formats without loss and markup changes
 2632
2632